I started a project to see if I could track smartphone users by sniffing for
wifi-clients. Most smartphones support wifi and most people don't bother disabling
wifi when they go outdoors1. If wifi is left on, it is possible to detect these
smartphones and track their movement. To be able to track smartphones, all I had
to do is grab a computer with a wifi card and start to listen for nearby
smartphones.
Over de course of 10 days I was able to detect around 590 unique wireless client
devices passing the vicinity of my house (near Amsterdam, The Netherlands).
Please note that not all of those devices are smartphones, so I have to
determine which are and which are not. I just used airmon-ng to sniff
for wifi clients.
It is very easy to track a person if wifi is enabled on their smartphone since
the phone will broadcast its unique identifier: its MAC-address. A MAC-address
is as unique as a phone number so ideal for tracking down people. A single wifi
sniffing computer is not enough to follow people, but if you would setup a grid
of wifi sniffing devices, tracking people would be very easy.
Then I got bored with this project and decided that if I could get any additional
information out of my data set of 590 wifi clients. The fun thing is that the
first tree parts of a MAC-address disclose the vendor of the device. For
instance, this MAC-address (made anonymous) belongs to HTC, thus is probably an
HTC smartphone.
90:27:E4:B7:XX:XX
There is a whole list that shows which MAC-addresses belong to which
manufacturers. This allows me to create a list of vendors associated with the
MAC-addresses I captured. This is fun, because I can now count how many devices
I 'caught' from a particular vendor.
The majority of wireless devices are from Apple (64%). The second largest is HTC
(12%). That is an incredible difference between number one and number two. If
these numbers actually mean anything, they are very interesting.
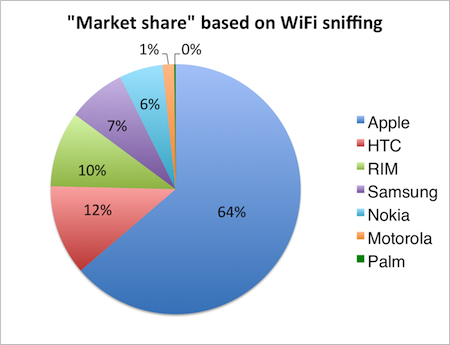
I think this picture is telling, but it's accuracy can be questioned. There are
some problems with my data set. For instance, maybe many people using a
particular brand of smartphone who do often disable wifi to conserve battery
life.
Also, look whose missing in this list: Sony Ericsson. Are Dutch people not
using Sony Ericsson smartphones? I must say that I deliberately used a Sony
Ericsson smartphone to test my setup and it detected the device without any
problem. So Sony Ericsson devices might not be that popular.
The main question is which conclusions can be drawn from this data: that iOS
users often leave their wifi enabled and more than other smartphone users?
It is difficult to say what this data actually means and how accurate it is, but
it may be an interesting technique none the less for real-life sampling of a
smartphone population.
1 Unless your phone is so crappy that it won't hold a charge through the day with wifi enabled.