[Update 2018] This article has been substantially updated since it was published in 2013.
Introduction
In this article, I will show you how to setup a Linux-based OpenVPN server. Once this server is up and running, I'll show you how to setup your iOS devices, such as your iPhone or iPad so that they can connect with your new VPN server.
The goal of this effort is to encapsulate all internet traffic through your VPN connection so no matter where you are, nobody can monitor which sites you visit and what you do. This is ideal if you have to visit the internet through untrusted internet sources like public Wi-Fi.
Some typical scenarios would be:
- you run an OpenVPN service on your Linux-based home router directly
- you run an OpenVPN service on a device behind your home router using portforwarding (like a Raspberry Pi)
- you run an OpenVPN service on a VPS hosted by one of many cloud service providers
Your iOS devices will be running OpenVPN Connect, a free application found in the App store.
A note on other platforms: Although this tutorial is focussed on iOS devices, your new OpenVPN-based VPN server will support any client OS, may it be Windows, MacOS, Android or Linux. Configuration of these other clients is out-of-scope for this article.
This tutorial is based on OpenVPN, an open-source product. The company behind OpenVPN also offers VPN services for a price per month. If you find the effort of setting up your own server too much of a hassle, you could look into their service. Please note that I have never used this service and cannot vouch for it.
This is a brief overview of all the steps you will need to take in order to have a fully functional setup, including configuration of the clients:
- Install a Linux server (out-of-scope)
- Install the OpenVPN software
- Setup the Certificate Authority
- Generate the server certificate
- Configure the OpenVPN server configuration
- Configure the firewall on your Linux server
- Generate certificates for every client (iPhone, iPad, and so on)
- Copy the client configuration to your devices
- Test your clients
How It Works
OpenVPN is an SSL-based VPN solution. SSL-based VPNs are very reliable because if you set it up properly, you will never be blocked by any firewall as long as TCP-port 443 is accessible. By default, OpenVPN uses UDP as a transport at port 1194, but you can switch to TCP-port 443 to increase the chance that your traffic will not be blocked at the cost of a little bit more bandwidth usage.
Authentication
Authentication is based on public/private key cryptography. The OpenVPN server is similar to an HTTPS server. The biggest difference is that your device doesn't use a username/password combination for authentication, but a certificate. This certificate is stored within the client configuration file.
So before you can configure and start your OpenVPN service, you need to setup a Certificate Authority (CA). With the CA you can create the server certificate for your OpenVPN server and after that's done, generate all client certificates.
OpenVPN installation
OpenVPN is available on most common Linux Distros by default. apt-get install openvpn for any Debian or Ubuntu version is all you need to install OpenVPN.
Or take a look here
I have never tried it out, but you can try and take a look at an OpenVPN install script
This script seems to automate a lot of steps, like firewall configuration, certificate generation, etc.
Tip
It's out-of-scope for this tutorial, but you should make sure that you keep your OpenVPN software up-to-date, in case security vulnerabilities are discovered in OpenVPN in the future.
Security
I'm creating this tutorial on an older system, with less secure default configuration settings for both the Certificate Authority as the OpenVPN server itself. The settings I use in this tutorial are based on the steps in this blog.
Notable improvements:
- AES256 for encryption
- 2048 bit key sizes over 1024 bit keys
- SHA256 over sha1/md5
Performance
I did some performance tests and got around 40-50 Mbs per iOS client. I believe that the bottleneck lies with my old HP Microserver N40L with its relatively weak CPU.
Traffic Shaping
If you want to limit how much bandwidth a client is allowed to use, I recommend to use this tutorial. I have tried it out and it works perfectly.
Creating a certificate authority.
For unbuntu: install the package "easy-rsa" and use the 'make-cadir' command instead of the setup instructions below.
I assume that you will setup your OpenVPN configuration in /etc/openvpn. Before you can setup the server configuration, you need to create a certificate authority. I used the folder /etc/openvpn/easy-rsa as the location for my CA.
mkdir /etc/openvpn/easy-rsa
We start with copying all these files to this new directory:
cp -R /usr/share/doc/openvpn/examples/easy-rsa/2.0* /etc/openvpn/easy-rsa
Please note that depending on your Linux flavour, these files may be found at some other path.
Next, we cd into the destination directory.
cd /etc/openvpn/easy-rsa
Now, open the 'vars' file with your favorite text editor. The following instructions are straight from the OpenVPN howto.
You should change all the values to ones that apply to you (obviously).
export KEY_COUNTRY="US"
export KEY_PROVINCE="California"
export KEY_CITY="San Fransisco"
export KEY_ORG="My Company"
export KEY_EMAIL="my@mail.com"
export KEY_CN=server
export KEY_NAME=server
export KEY_OU=home
Change the KEY_SIZE parameter:
export KEY_SIZE=2048
How long would you like your certificates to be valid (10 years?)
export CA_EXPIRE=3650
export KEY_EXPIRE=3650
Then I had to copy openssl-1.0.0.cnf to openssl.cnf because the 'vars' script complained that it couldn't find the latter file.
cp openssl-1.0.0.cnf openssl.cnf
Notice I went through these steps on an older Linux installation. I had to edit the file /etc/openvpn/easy-rsa/pkitool and changed all occurrences of 'sha1' to 'sha256'.
Now we 'source' var and run two additional commands that actually generate the certificate authority. Notice the dot before ./vars.
. ./vars
./clean-all
./build-ca
./build-dh
You will have to confirm the values or change them if necessary.
Now we have a certificate authority and we can create new certificates that will be signed by this authority.
WARNING: be extremely careful with all key files, they should be kept private.
I would recommend performing these commands:
chown -R root:root /etc/openvpn
chmod -R 700 /etc/openvpn
By default, OpenVPN runs as root. With these commands, only the root user will be able to access the keys. If you don't run OpenVPN as root, you must select the appropriate user for the first command. See also this article.
Creating the Server Certificate
We create the server certificate:
./build-key-server server
It's up to you to come up with an alternative for 'server'. This is the file name under which the key files and certificates are stored.
All files that are generated can be found in the '/etc/openvpn/easy-rsa/keys' directory. This is just a flat folder with both the server and client keys.
Creating the optional TLS-AUTH Certificate
This step is optional but it doesn't take much effort and it seems to add an additional security layer at no significant cost. In this step we create an additional secret key that is shared with both the server and the clients.
The following steps are based on this article (use of -tls-auth).
cd /etc/openvpn/easy-rsa/keys
openvpn --genkey --secret ta.key
When we are going to create the server configuration, we will reference this key file.
Creating the Client Certificate
Now that we have a server certificate, we are going to create a certificate for our iPhone (or any other iOS device).
./build-key iphone
Answer the questions with the defaults. Don't forget to answer these questions:
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
So now we have everything in place to start creating an OpenVPN configuration. We must create a configuration for the server and the client. Those configurations are based on the examples that can be find in /usr/share/doc/openvpn/examples/.
Example Server configuration
This is my server configuration which is operational. It is stored in /etc/openvpn/openvpn.conf
dev tun2
tls-server
cipher AES-256-CBC
auth SHA256
remote-cert-tls client
dh easy-rsa/keys/dh2048pem
ca easy-rsa/keys/ca.crt
cert easy-rsa/keys/server.crt
key easy-rsa/keys/server.key
tls-auth easy-rsa/keys/ta.key
server 10.0.0.0 255.255.255.0
log /var/log/openvpn.log
script-security 2
route-up "/sbin/ifconfig tun2 up"
port 443
proto tcp-server
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
I believe you should be able to use this configuration as-is. Depending on your local IP-addresses within your own network, you may have to change the server section.
I use TCP-port 443 as this destination port is almost never blocked as blocking this port would break most internet connectivity. (The downside is that I can no longer host any secure web site on this IP-address).
The OpenVPN service will provide your client with an IP-address within the address range configured in the 'server' section.
Change any parameters if required and then start or restart the OpenVPN service:
/etc/init.d/openvpn restart
Make sure that the server is running properly in /var/log/openvpn.log
If you want to use your VPN to browse the internet, we still need to configure a basic firewall setup.
I'm assuming that you already have some kind of IPtables-based firewall running. Configuring a Linux firewall is out-of-scope for this article. I will only discuss the changes you may need to make for the OpenVPN service to operate properly.
You will need to accept traffic to TCP port 443 on the interface connected to the internet.
iptables -A INPUT -p tcp -m tcp --dport 443 -j ACCEPT
If your OpenVPN server is behind a router/firewall, you need to configure port-forwarding on that router/firewall. How to do so is out-of-scope for this article, as it is different for different devices.
Assuming that you will - for example - use the 10.0.0.0/24 network for VPN clients such as your iPhone, you must also create a NAT rule so VPN clients can use the IP-address of the Linux server to access Internet.
iptables -t nat -A POSTROUTING -s "10.0.0.0/24" -o "eth0" -j MASQUERADE
Please note that you must change eth0 with the name of the appropriate interface that connects to the internet. Change the IP-address range according to your own situation. It should not conflict with your existing network.
iptables -A FORWARD -p tcp -s 10.0.0.0/24 -d 0.0.0.0/0 -j ACCEPT
Please note that I haven't tested these rules, as I have a different setup. But this should be sufficient. And make sure that forwarding is enabled like this:
echo 1 > /proc/sys/net/ipv4/ip_forward
Example Client configuration
Most OpenVPN clients can automatically import files with the .ovpn file extension. A typical configuration file is something like 'iphone.ovpn'.
Warning: the .ovpn files will contain the certificate used by your iPhone/iPad to authenticate against your OpenVPN server. Be very carefull where you store this file. Anyone that is able to obtain a copy of this file, will be able to connect to your VPN server.
This is an example configuration file, but we are not going to create it by hand, it's too much work.
What you will notice from this example is that the .ovpn file contains both the client configuration and all the required certificates:
- the CA root certificate
- the server certificate to validate the server
- the client private certificate
- the TLS-AUTH certificate (an optional extra security measure)
Create a client configuration file (.ovpn) with a script
You can create your client configuration file manually but that is a lot of work. Because you need to append all the certificates to a single file, that also contains the configuration settings.
So we will use a script to setup the client configuration.
First we are going to create a folder where our client configuration files will be stored.
mkdir /etc/openvpn/clientconfig
chmod 700 /etc/openvpn/clientconfig
Now we will download the script and the accompanying configuration template file. Notice that the links may wrap.
cd /etc/openvpn
wget https://raw.githubusercontent.com/louwrentius/openvpntutorial/master/create-client-config.sh
wget https://raw.githubusercontent.com/louwrentius/openvpntutorial/master/client-config-template
chmod +x create-client-config.sh
Please note that you first need to create the certificates for your devices before you can generate a configuration file. So please go back to that step if you need to.
Also take note of the name you have used for your devices. You can always take a look in /etc/openvpn/easy-rsa/keys to see how your devices are called.
Now, edit this client-config-template and change the appropriate values where required. You may probably only need to change the first line:
remote <your server DNS address or IP address>
Now you are ready to run the script and generate the config file for your device.
When you run this script, a configuration file is generated and placed in to the folder /etc/openvpn/clientconfig.
The script just puts the client configuration template and all required certificates in one file. This is how you use it:
./create-client-config.sh iPhone
Some output you will notice when running the script:
user@server:/etc/openvpn# ./create-client-config.sh iphone
Client's cert found: /etc/openvpn/easy-rsa/keys/iphone
Client's Private Key found: /etc/openvpn/easy-rsa/keys/iphone.key
CA public Key found: /etc/openvpn/easy-rsa/keys/ca.crt
tls-auth Private Key found: /etc/openvpn/easy-rsa/keys/ta.key
Done! /etc/openvpn/clientconfig/iphone.ovpn Successfully Created.
You should now find a file called 'iphone.ovpn' in the directory /etc/openvpn/clientconfig.
We are almost there. We just need to copy this file to your iOS device.
You have three options:
- Use iCloud Drive
- Use iTunes
- Use email (obviously insecure and not discussed)
Setting up your iPhone or iPad with iCloud Drive
- First install the OpenVPN Connect application if you haven't done so.
- Copy the .ovpn file from your OpenVPN server to your iCloud Drive.
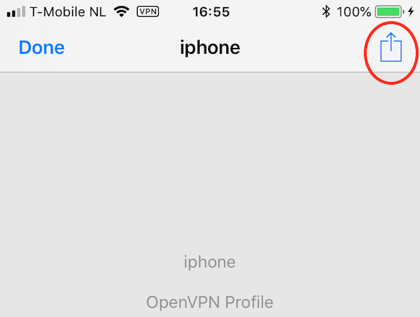
- Take your device and use the 'files' browser to navigate within your iCloud drive to the .ovpn file you just copied.
- Tap on the file to download and open it.
- Now comes the tricky part: press the share symbol
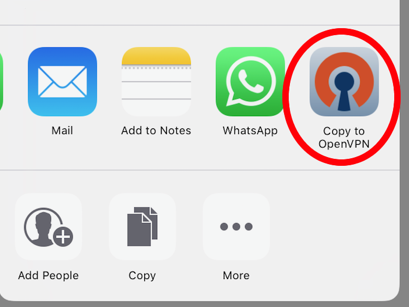
Open the file with the OpenVPN application on your iOS device:
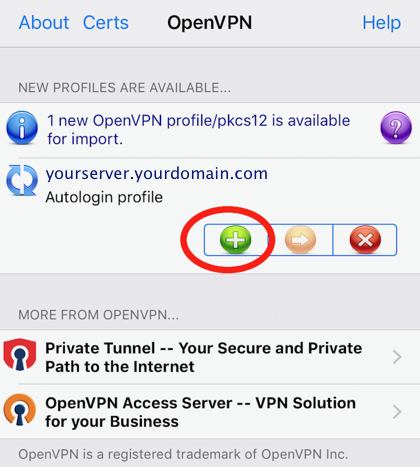
When you get the question "OpenVPN would like to Add VPN Configurations", choose 'Allow'.
Continue with the step 'Test your iOS device'.
If the OpenVPN Connect client doesn't import the file, remove the application from the device and re-install it. (This is what I had to do on my iPad).
Setting up your iPhone or iPad with iTunes
You can skip this step if you used iCloud Drive to copy the .ovpn profile to your device.
You need to get the following files on your iOS device:
iphone.ovpn
Copy this file from your OpenVPN server to the computer running iTunes. Then connect your device to iTunes with a cable.
- Open iTunes
- Select your device at the top right
- Go to the Apps tab
- Scroll to the file sharing section
- Select the OpenVPN application
- Add the iphone.ovpn
- Sync your device
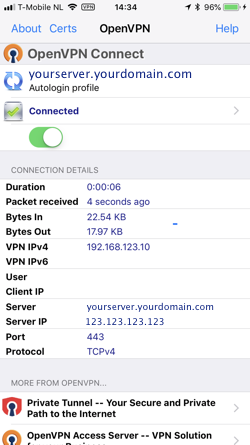
Test your iOS device
Open the OpenVPN client. You will see a notice that a new configuration has been imported and you need to accept this configuration.
As it might not work straight away, you need to monitor /var/log/openvpn.log on the server to watch for any errors.
Now try to connect and enjoy.
Conclusion
You should be able to keep your VPN enabled at all times because battery usage overhead should be minimal. If you are unable to connect to your VPN when you are at home behind your own firewall, you need to check your firewall settings.
Updated 20130123 with keepalive option. Updated 20130801 with extra server push options for traffic redirection and DNS configuration Updated 20180618 as substantial rewrite of the original outdated article.


Comments